Beschrijving
This plugin determines whether any of your plugins or themes have security vulnerabilities. It does this by looking up details in the WPScan Vulnerability Database.
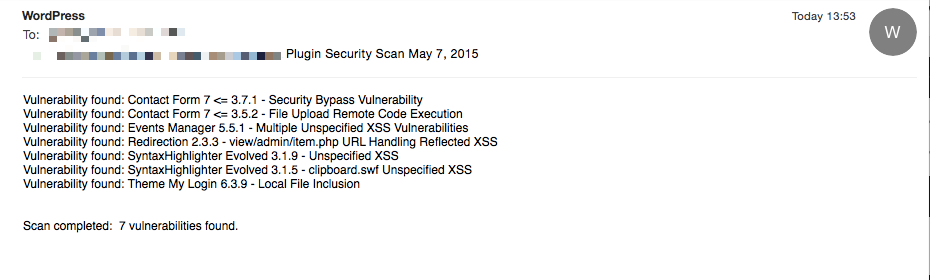
It will run a scan once a day, and e-mail the administrator if any vulnerable plugins or themes are found.
Please note: As from version 2.0.0, you will need to register on the WPScan Vulnerability Database site in order to get an API token. This token is required before any security scans can be performed. Once you have your token, it can be added to the Plugin Security Scanner settings page.
You can also register a webhook for notifications. The webhook will trigger daily, even if no vulnerabilities found. The webhook is a post request, with JSON payload containing the vulnerabilities.
You can enable the webhook under Settings\General tab – see the Plugin Security Scanner settings.
It also adds a new menu option to the admin tools menu called “Plugin Security Scanner”. Clicking this runs a scan. If the scan finds any problems, it shows you a list of plugins or themes that have vulnerabilities, along with a description of the issue.
The WPScan Vulnerability Database API, which this plugin uses, is free for non-commercial use. However, any commercial usage will require that you purchase a commercial license from WPScan. If you are using the API for your own site then you will not need a commercial license. However, if you are a hosting company and install the plugin systematically across all of your clients sites, then you will need to purchase a commercial license. If you are making heavy use of the API, it is likely that you will need to purchase a commercial license. To enquire about a commercial license, please contact team@wpvulndb.com
Icons made by Alessio Atzeni from www.flaticon.com is licensed by CC BY 3.0
Schermafbeeldingen
Beoordelingen
Bijdragers & ontwikkelaars
“Plugin Security Scanner” is open source software. De volgende personen hebben bijgedragen aan deze plugin.
BijdragersVertaal “Plugin Security Scanner” naar jouw taal.
Interesse in ontwikkeling?
Bekijk de code, haal de SVN repository op, of abonneer je op het ontwikkellog via RSS.
Changelog
2.0.2
- Clarified 403 error
2.0.1
- Clarified error message in daily email
2.0.0
- Use WPScan Vulnerability Database API V3
- Important notice: to use this plugin, you now need to register a user and get an API token from https://wpvulndb.com/users/sign_up
- Improved error handling
1.6.0
- Moved settings to dedicated page
- Added option to ignore unpatched issues
1.5.2
- Fix: Allow scanning if you are running WordPress nightly or release candidates
1.5.1
- Added option to ignore ‘WordPress 2.3-4.8.3 – Host Header Injection in Password Reset’ vulnerability
1.5.0
- Checks vulnerabilities in WordPress core files
- Added ability to send an HTTP request when vulnerabilities are found (webhook)
1.4.1
- Fix issue with theme version checking
1.4
- Themes as well as plugins are now scanned for vulnerabilities
1.3.1
- Added check to make sure the WPVulnDb API has returned a valid response
1.3
- Added option under “Settings / General / Plugin Security Scanner” to disable the email notification
1.2.1
- Moved to WPScan Vulnerability Database API v2
1.2.0
- Added i18n support
1.1.9
- Fix: Removed unecessary ob_flush calls
- Fix: If vulnerability does not have a “fixed in” version number, report it as a vulnerability
1.1.8
- Fix: corrected links to WPScan Vulnerability Database
1.1.7
- Add link to WPScan Vulnerability Database details page
1.1.6
- Conditionally include plugin.php include in case it is not already included
1.1.5
- Escape output in HTML report to prevent XSS
1.1.4
- Added blog title to email subject
1.1.3
- Fixed bug that prevented admin email being sent
1.1
- Email admin daily if any vulnerabilities are found
1.0
- Initial release